A crimeware-related threat actor known as Haskers Gang has released an information-stealing malware called ZingoStealer for free on, allowing other criminal groups to leverage the tool for nefarious purposes.
„It features the ability to steal sensitive information from victims and can download additional malware to infected systems,” Cisco Talos researchers Edmund Brumaghin and Vanja Svajcer said in a report shared with The Hacker News.
„In many cases, this includes the RedLine Stealer and an XMRig-based cryptocurrency mining malware that is internally referred to as 'ZingoMiner.'”
But in an interesting twist, the criminal group announced on Thursday that the ownership of the ZingoStealer project is changing hands to a new threat actor, in addition to offering to sell the source code for a negotiable price of $500.
Since its inception last month, ZingoStealer is said to be undergoing consistent development and deployed specifically against Russian-speaking victims by packaging it as game cheats and pirated software. Haskers Gang is known to be active since at least January 2020.
Besides harvesting sensitive information such as credentials, stealing cryptocurrency wallet information, and mining cryptocurrency on victims’ systems, the malware leverages Telegram as both an exfiltration channel as well as a platform to distribute updates.
Customers of the product can opt to pay about $3 to encase the malware in a custom crypter called ExoCrypt that makes it possible to evade antivirus defenses without having to rely on a third-party crypter solution.
The incorporation of the XMRig cryptocurrency mining software into the stealer, the researchers said, is an attempt on the part of the malware author to further monetize their efforts by using systems infected by affiliates to generate Monero coins.
Malicious campaigns delivering the malware take the form of a game modification utility or a software crack, with the threat actors posting YouTube videos advertising the tools’ features and its description, including a link to an archive file hosted on Google Drive or Mega that contains the ZingoStealer payload.
That said, Cisco Talos pointed out that the executables are also being hosted on the Discord CDN, raising the possibility that the infostealer is being disseminated within gaming-related Discord servers.
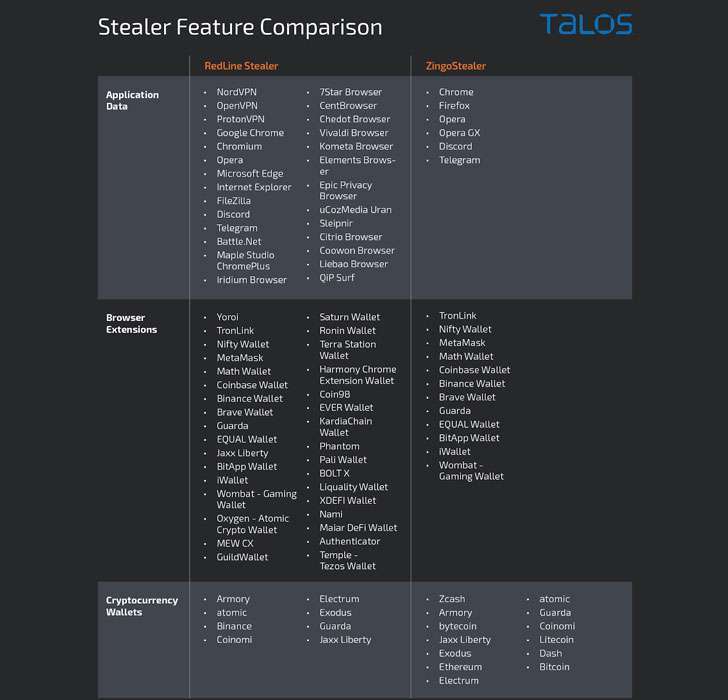
ZingoStealer, for its part, is fashioned as a .NET binary that’s capable of collecting system metadata and information stored by web browsers such as Google Chrome, Mozilla Firefox, Opera, and Opera GX, while also siphoning details from cryptocurrency wallets.
What’s more, the malware is equipped to deploy secondary malware at the discretion of the attacker, such as RedLine Stealer, a more feature-rich information stealer that plunders data from various applications, browsers, and cryptocurrency wallets and extensions. This potentially may explain why the malware authors are offering ZingoStealer for free to any adversary.
„Users should be aware of the threats posed by these types of applications and should ensure that they are only executing applications distributed via legitimate mechanisms,” the researchers said.




